Your Key to Swift Data Restoration
Expert Ransomware Recovery Service
Welcome to our professional Ransomware Recovery Service, where we specialize in swift and reliable data restoration after a cyber attack. With our seasoned team of experts, we understand the urgency of recovering your valuable data and ensuring business continuity.

Why Choose Our Ransomware Recovery Service?
The process of decrypting data encrypted by ransomware is known as ransomware recovery. Every case is different; depending on the situation, we may respond on-site, but most of the time, we use remote access to get into the compromised systems.We prioritize the needs of the client. It may involve data carving, cleanup, digital forensics, environment security, etc.
When possible, Proven Data collaborates with your MSP or IT staff to speed up system and data restoration.
1. Proven Expertise:
- Our seasoned professionals have a track record of successful ransomware recovery, restoring data for businesses of all sizes and industries.
- Years of experience in dealing with various ransomware strains and evolving cyber threats.
2. Rapid Response:
- Time is critical in ransomware recovery. Our rapid response team is available 24/7 to initiate the recovery process immediately upon detection of an attack.
- Swift action minimizes downtime and prevents further data loss.
3. Tailored Solutions:
- Every ransomware attack is unique. We provide personalized recovery plans tailored to your organization’s specific needs and the nature of the ransomware involved.
- Customized strategies ensure a targeted and effective recovery process.
4. Cutting-edge Technology:
- We leverage the latest in cybersecurity technology to detect and neutralize ransomware threats.
- Advanced tools and methodologies ensure comprehensive data restoration without compromising data integrity.
5. Transparent Communication:
- Stay informed at every step. Our transparent communication ensures you are aware of the recovery progress, timelines, and any potential challenges.
- We prioritize open and clear communication to provide peace of mind during the recovery process.



Secure your business's swift recovery and fortify against future threats
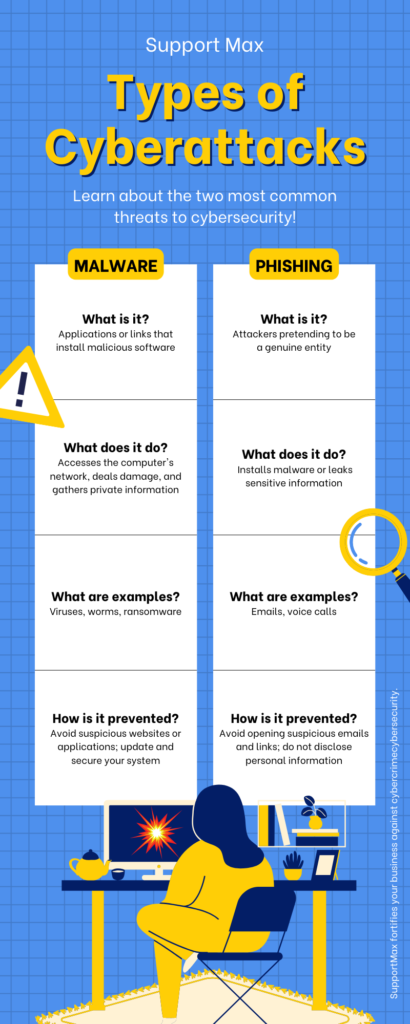
Ransomware is a type of malicious software designed to block access to a computer system or files until a sum of money, typically in cryptocurrency, is paid to the attackers. It works by encrypting the victim’s files or locking them out of their system, rendering the data inaccessible. Cybercriminals often deliver ransomware through phishing emails, malicious websites, or exploiting vulnerabilities in software. Once the victim’s files are encrypted, a ransom demand is issued, and payment is demanded in exchange for a decryption key. Ransomware attacks can have severe consequences, leading to data loss, financial damage, and disruptions to business operations. Preventative measures, including robust cybersecurity practices and regular backups, are crucial in mitigating the risks associated with ransomware.
Identifying a ransomware attack requires vigilance and an awareness of potential warning signs. Here are key indicators that may suggest a ransomware incident:
1. Unexpected File Encryption:
– Sudden, unexplained encryption of files on your system, making them inaccessible.
2. Changed File Extensions:
– Altered file extensions, such as .locky, .crypt, or .encrypted, indicating potential ransomware.
3. Ransom Notes:
– Finding text or HTML files demanding payment for file decryption, often accompanied by instructions on how to pay.
4. Unusual Network Traffic:
– Anomalies in network traffic, especially to unfamiliar domains or IP addresses.
5. Slow System Performance:
– A significant decrease in computer or network performance due to the encryption process.
6. Disabled Security Software:
– Inability to access or update antivirus and security software, as ransomware often targets these programs.
7. Pop-up Messages:
– Unexpected messages demanding payment for the release of files or threatening data deletion.
8. Unusual User Permissions:
– Unauthorized changes in user privileges or the creation of new accounts.
9. Unrecognized Programs:
– Presence of unknown or suspicious programs on your system.
10. Phishing Emails:
– Receipt of phishing emails with malicious attachments or links that may introduce ransomware.
11. Altered File Timestamps:
– Changes in the timestamps of files, indicating potential unauthorized modifications.
12. Unexplained System Reboots:
– Random system reboots or shutdowns without user initiation.
If you observe any of these signs, it’s crucial to act swiftly:
– Isolate Infected Systems:
– Disconnect affected devices from the network to prevent the ransomware from spreading.
– Report and Seek Assistance:
– Inform your IT department or a cybersecurity professional to assess and address the situation.
– Do Not Pay the Ransom:
– Law enforcement agencies and cybersecurity experts generally advise against paying ransoms, as it does not guarantee data recovery and may support criminal activities.
Preventative measures, such as regular backups, employee training, and up-to-date security software, can also significantly reduce the risk of falling victim to a ransomware attack.
SupportMax stands out in ransomware recovery with a combination of unique features and a client-centric approach:
Proven Expertise:
- A team of seasoned professionals with a demonstrated track record of successful ransomware recoveries.
Rapid Response Team:
- A 24/7 rapid response team ready to initiate recovery processes immediately, minimizing downtime and data loss.
Tailored Solutions:
- Personalized recovery plans designed to meet the specific needs of each client, ensuring a targeted and effective recovery process.
Cutting-edge Technology:
- Utilization of the latest cybersecurity technology, including advanced tools and methodologies, to detect and neutralize ransomware threats.
Transparent Communication:
- Open and clear communication throughout the recovery process, keeping clients informed about progress, timelines, and potential challenges.
Preventative Measures:
- Beyond recovery, SupportMax offers guidance on preventative measures and ongoing support to fortify clients against future ransomware attacks.
Client Testimonials:
- Positive feedback and testimonials from satisfied clients who have experienced successful ransomware recoveries with SupportMax.
Industry Recognition:
- Recognition and positive reviews from industry experts and organizations for the effectiveness and reliability of SupportMax’s ransomware recovery services.
Continuous Learning and Adaptation:
- A commitment to staying abreast of evolving cybersecurity trends, ensuring that SupportMax’s methods are always aligned with the latest threats and best practices.
Customer-Centric Approach:
- A dedication to providing comprehensive, customer-focused solutions that go beyond recovery, emphasizing the importance of long-term cybersecurity resilience.
By combining technical expertise, a rapid response model, and a commitment to client satisfaction, SupportMax provides a comprehensive and effective approach to ransomware recovery, setting it apart as a trusted leader in the field.
If you suspect a ransomware attack, taking immediate and decisive action is crucial. Here are the steps you should consider:
Isolate Infected Systems:
- Disconnect the affected devices from the network to prevent the ransomware from spreading to other systems.
Shut Down and Preserve Systems:
- Power down infected devices to preserve data and prevent further encryption. This step is particularly important for shared network drives.
Alert IT and Security Teams:
- Notify your IT department and security teams immediately so they can assess the situation and initiate the response plan.
Contact Law Enforcement:
- Report the incident to law enforcement agencies, such as local police or your country’s cybercrime division. Provide them with all relevant details.
Do Not Pay the Ransom:
- Law enforcement agencies and cybersecurity experts generally advise against paying ransoms. Payment does not guarantee data recovery and may further support criminal activities.
Document the Ransom Note:
- Take screenshots or document the ransom note and any communication received from the attackers. This information may be valuable for law enforcement investigations.
Restore from Backup:
- If you have recent and clean backups, restore your systems from these backups to minimize data loss. Ensure that the backups are not compromised.
Scan and Clean Systems:
- Conduct thorough antivirus and antimalware scans on all systems to remove any remnants of the ransomware. Ensure that systems are clean before reconnecting them to the network.
Implement Security Improvements:
- Identify and address vulnerabilities that may have allowed the ransomware to infiltrate your systems. Update software, patch vulnerabilities, and enhance security measures.
Communicate Internally:
- Inform employees and stakeholders about the incident, emphasizing the importance of vigilance in the face of potential phishing or social engineering attempts.
Engage Ransomware Recovery Experts:
- Consider engaging professional ransomware recovery services, like SupportMax, to assess the extent of the damage and assist in the recovery process.
Learn from the Incident:
- Conduct a post-incident analysis to understand how the ransomware infiltrated your systems. Use this information to improve your cybersecurity posture and prevent future attacks.
Remember, time is of the essence in responding to a ransomware attack. The sooner you act, the better chance you have of minimizing damage and recovering your data.
he ransomware recovery process involves several key steps to efficiently restore systems and data. Here is an overview of how the recovery process typically works:
Assessment:
- Immediate Response: Engage a rapid response team to assess the extent of the ransomware attack and identify affected systems.
- Scope Analysis: Evaluate the impact on data, systems, and potential vulnerabilities.
Isolation and Containment:
- Disconnect Systems: Isolate infected systems from the network to prevent further spread of the ransomware.
- Containment Strategies: Implement strategies to contain the ransomware and minimize its impact on other systems.
Identification of Ransomware Variant:
- Determine the specific ransomware variant involved, as this information can guide the recovery strategy.
Communication with Attackers:
- In some cases, cybersecurity experts may attempt to communicate with the attackers to gather information, negotiate, or explore possible decryption solutions.
Data Restoration Planning:
- Develop a prioritized plan for restoring critical data, considering factors such as business impact, importance of data, and recovery time objectives (RTO).
Backup Restoration:
- Utilize clean and recent backups to restore affected data. Ensure backups are free from the ransomware and perform thorough checks to maintain data integrity.
Security Auditing and Improvements:
- Conduct a security audit to identify vulnerabilities that allowed the ransomware to penetrate systems.
- Implement security improvements, such as software updates, patches, and enhanced security measures, to prevent future attacks.
Post-Recovery Testing:
- Test restored systems to ensure functionality and security. Verify that all critical data is accessible and that systems operate as expected.
User Education and Awareness:
- Educate employees about the incident, emphasizing the role they play in preventing future ransomware attacks through awareness and vigilance.
Documentation and Reporting:
- Document the entire recovery process, detailing actions taken, lessons learned, and recommendations for future prevention.
- Report the incident to relevant authorities, if required by law.
Ongoing Monitoring and Prevention:
- Implement continuous monitoring of systems to detect any residual threats or potential signs of future attacks.
- Establish and enforce robust cybersecurity measures to prevent ransomware and other cyber threats.
Engagement with Ransomware Recovery Experts:
- Collaborate with professional ransomware recovery services, such as SupportMax, to ensure a thorough and effective recovery process.
Throughout the recovery process, collaboration with cybersecurity experts and adherence to best practices are critical to achieving a successful outcome and strengthening defenses against future threats.
Certainly, SupportMax is dedicated to not only recovering from ransomware attacks but also preventing future incidents. Here’s how SupportMax can help prevent future ransomware attacks:
Comprehensive Security Assessments:
- Conduct thorough security assessments to identify vulnerabilities in your systems and network.
- Analyze existing security protocols and recommend improvements to enhance overall resilience.
Employee Training and Awareness:
- Provide targeted training sessions for employees to educate them about phishing threats, social engineering tactics, and best practices for maintaining a secure digital environment.
- Raise awareness about the consequences of ransomware attacks and the role employees play in preventing them.
Endpoint Protection:
- Implement advanced endpoint protection solutions to detect and block ransomware before it can execute on endpoints.
- Regularly update and configure endpoint security measures to adapt to evolving threats.
Network Security Enhancement:
- Strengthen network security through the implementation of firewalls, intrusion detection systems, and other protective measures.
- Regularly review and update network security policies to align with emerging threats.
Data Backup and Recovery Planning:
- Develop and implement robust data backup and recovery strategies to ensure the availability of clean, recent backups.
- Regularly test backup restoration processes to verify their effectiveness.
Security Patching and Updates:
- Monitor and apply timely security patches and updates for operating systems, software, and applications to address known vulnerabilities.
- Establish a systematic approach to keep systems up-to-date and resilient against emerging threats.
Incident Response Planning:
- Collaborate with organizations to create and refine incident response plans, ensuring a swift and effective response in the event of a security incident.
- Conduct regular drills and simulations to test the preparedness of the response team.
Continuous Monitoring and Threat Intelligence:
- Implement continuous monitoring tools to detect and respond to anomalies in real-time.
- Stay abreast of the latest threat intelligence to proactively address emerging ransomware variants and tactics.
Regular Security Audits:
- Conduct periodic security audits to assess the effectiveness of existing security measures.
- Identify and rectify potential weaknesses before they can be exploited.
Ongoing Support and Updates:
- Provide ongoing support to clients, offering updates on the latest cybersecurity trends and threats.
- Remain available for consultations and assistance in adapting security measures based on the evolving threat landscape.
By combining preventative measures with ongoing support and education, SupportMax aims to create a resilient security posture for organizations, reducing the risk of ransomware attacks and ensuring a proactive defense against emerging threats.
Ransomware recovery may be covered by insurance, but the specifics depend on the type of insurance policies a business has in place. Here are some key points to consider:
Cybersecurity Insurance:
- Many businesses invest in cybersecurity insurance to protect against financial losses resulting from cyber incidents, including ransomware attacks.
- Cyber insurance policies may cover costs related to ransom payments, legal fees, public relations efforts, and the expenses associated with recovering and restoring data.
Policy Terms and Conditions:
- The coverage for ransomware recovery can vary significantly among insurance providers and policies.
- It’s crucial to carefully review the terms and conditions of the insurance policy to understand the scope of coverage, limitations, and any specific requirements that must be met.
Notification and Reporting Requirements:
- Some insurance policies may require prompt notification and reporting of a ransomware incident. Failure to adhere to these requirements could impact the coverage.
Negotiation Costs:
- Insurance coverage may extend to cover the costs associated with negotiating with cybercriminals, including engaging professional negotiators.
Business Interruption Coverage:
- Business interruption coverage within a cybersecurity insurance policy may compensate for the financial losses incurred during the downtime caused by a ransomware attack.
Data Restoration and Recovery Costs:
- Expenses related to data restoration and recovery, including hiring external experts and services, may be covered by insurance.
Exclusions and Deductibles:
- Policies may have exclusions for certain types of cyber incidents or deductibles that the insured party must pay before coverage kicks in.
- Understanding these exclusions and deductibles is essential for managing expectations regarding insurance coverage.
Risk Mitigation Measures:
- Some insurance providers may offer better terms or discounts for businesses that demonstrate proactive cybersecurity measures and risk mitigation strategies.
Legal and Regulatory Compliance:
- Insurance coverage may assist with the costs associated with legal and regulatory compliance following a ransomware attack.
Engagement with Insurance Experts:
- It is advisable to engage with insurance experts or brokers who specialize in cybersecurity insurance to ensure that businesses have appropriate coverage tailored to their needs.
It’s crucial for businesses to work closely with their insurance providers and legal advisors to fully understand the implications of their coverage in the event of a ransomware attack. Regularly reviewing and updating insurance policies to align with the evolving threat landscape is also recommended.
Ransomware recovery services are essential for businesses across various industries, as any organization with digital assets is vulnerable to cyber threats. Specific industries and businesses that can benefit significantly from ransomware recovery services include:
Healthcare Providers:
- Hospitals, clinics, and healthcare facilities store sensitive patient data that is highly valuable to cybercriminals.
Financial Institutions:
- Banks, credit unions, and financial service providers are prime targets due to the sensitive financial information they possess.
Government Agencies:
- Federal, state, and local government entities store vast amounts of sensitive information that, if compromised, can have severe consequences.
Educational Institutions:
- Schools, colleges, and universities store student and staff information, making them potential targets for ransomware attacks.
Manufacturing and Industrial Sectors:
- Companies in manufacturing and industrial sectors are increasingly reliant on digital systems, and a ransomware attack can disrupt production and supply chains.
Retail and E-commerce Businesses:
- Retailers and online businesses store customer data and financial information, making them attractive targets for cybercriminals.
Legal Firms:
- Law firms often handle sensitive client information, and a ransomware attack can compromise client confidentiality.
Technology Companies:
- Tech firms, including software developers and IT service providers, may be targeted due to their access to valuable intellectual property.
Professional Services:
- Businesses providing professional services, such as consulting firms, accounting firms, and marketing agencies, may store sensitive client data.
Nonprofit Organizations:
- Nonprofits, like any other organization, may become victims of ransomware attacks, potentially jeopardizing donor and beneficiary information.
Energy and Utilities:
- Companies in the energy and utilities sector are critical infrastructure entities, and a ransomware attack can have severe consequences on service delivery.
Transportation and Logistics:
- Transportation and logistics companies may face disruptions to their operations if critical systems are compromised by ransomware.
Hospitality and Tourism:
- Hotels, travel agencies, and tourism-related businesses handle customer data and financial transactions, making them potential targets.
Small and Medium-sized Enterprises (SMEs):
- SMEs, regardless of industry, are often targeted due to perceived vulnerabilities, and their recovery efforts can benefit from professional ransomware recovery services.
Given the widespread nature of ransomware threats, businesses of all sizes and industries should prioritize cybersecurity and have a recovery plan in place. Engaging with professional ransomware recovery services, such as SupportMax, can provide tailored solutions to mitigate the impact of attacks and enhance overall cybersecurity resilience.
Absolutely, SupportMax understands the critical nature of ransomware incidents, and our recovery services are available 24/7 to ensure swift and responsive assistance for our clients. We prioritize accessibility and immediate action in the face of cyber threats, recognizing that time is of the essence in mitigating the impact of a ransomware attack.
Key aspects of SupportMax’s 24/7 ransomware recovery services include:
Rapid Response Team:
- Our dedicated rapid response team is on standby around the clock, ready to initiate the recovery process immediately upon notification of a ransomware incident.
Immediate Action:
- Time is a critical factor in mitigating the effects of a ransomware attack. SupportMax acts promptly to isolate affected systems, contain the threat, and minimize further damage.
Continuous Monitoring:
- We implement continuous monitoring to detect and respond to any emerging threats or potential signs of ransomware attacks in real-time.
Global Reach:
- SupportMax’s 24/7 services are accessible globally, ensuring that clients in different time zones receive the same level of immediate attention and support.
Expert Consultation:
- Our team of seasoned professionals is available for expert consultation at any hour, providing guidance, reassurance, and a comprehensive understanding of the recovery process.
Transparent Communication:
- Clear and transparent communication is maintained throughout the recovery process, keeping clients informed about progress, challenges, and steps being taken to restore their systems.
Customized Recovery Plans:
- SupportMax tailors recovery plans to the specific needs of each client, recognizing that every ransomware incident is unique. Our 24/7 availability ensures personalized and effective solutions.
By emphasizing accessibility and responsiveness, SupportMax aims to instill confidence in our clients, assuring them that they have a reliable partner ready to assist at any time, day or night, in the event of a ransomware attack.
SupportMax’s ransomware recovery consultation is designed to gather comprehensive information about the incident, ensuring a thorough understanding of the situation and facilitating an effective recovery process. Here is what we typically need during an initial ransomware recovery consultation:
Incident Overview:
- Provide a detailed overview of the ransomware incident, including when it was first identified, the affected systems, and any immediate actions taken.
Ransom Note and Communication:
- Share any ransom notes or communications received from the attackers. Include details such as ransom amount, payment instructions, and deadlines.
System Information:
- Identify the systems and networks affected by the ransomware. Provide details on the types of data compromised and the criticality of the affected systems to your operations.
Backup and Recovery Practices:
- Describe your existing backup and recovery practices, including the frequency of backups, storage locations, and the last known clean backup.
Security Measures in Place:
- Detail the cybersecurity measures currently in place, such as antivirus software, firewalls, and intrusion detection systems.
Network Architecture:
- Provide an overview of your network architecture, including the layout of servers, workstations, and any interconnected devices.
User Access and Permissions:
- Detail user access controls and permissions to understand how the ransomware may have propagated through your network.
Recent System Changes:
- Share information on any recent system changes, updates, or installations that might be relevant to the ransomware incident.
Employee Training and Awareness:
- Describe the level of cybersecurity training and awareness among your employees. This helps in assessing the potential vectors through which the ransomware may have entered.
Legal and Regulatory Obligations:
- Discuss any legal or regulatory obligations related to data breaches or cyber incidents. This information helps tailor the recovery process to comply with relevant laws and regulations.
Budget and Constraints:
- Share information about budgetary constraints and any other limitations that may impact the recovery process. This allows us to provide solutions within your financial parameters.
By gathering this information during the ransomware recovery consultation, SupportMax aims to conduct a thorough analysis, customize recovery plans, and provide expert guidance to address the unique aspects of each ransomware incident. Transparency, collaboration, and a detailed understanding of the situation are key elements in formulating an effective recovery strategy.
Specializing in Mitigating Common Ransomware Threats