
In 2023, a cyberattack occurred every 39 seconds. That’s not just a staggering number—it’s a reality check. Cybersecurity isn’t just an industry buzzword or a vague concept for the IT team to deal with. It’s the very backbone of your digital safety and business continuity. So how does it actually work? Not in theory, but in practice? Let’s break it down.
Cybersecurity is about more than just firewalls and antivirus software. It’s a combination of tools, processes, and—perhaps most importantly—people working together to protect sensitive information from bad actors. It’s about staying one step ahead of the evolving threats, understanding vulnerabilities, and building systems that aren’t just reactive but proactive.
Join me, and we’ll dig into the mechanics of how cybersecurity really works. By the end of this article, you’ll have a clear sense of the strategies and technologies protecting your data, plus actionable steps to fortify your own systems.
The Core Pillars of Cybersecurity: What’s at Stake?
To understand how cybersecurity works, we need to start with the core pillars that underpin it. Effective cybersecurity revolves around three main elements:
- Confidentiality: Ensuring that sensitive information is only accessible to authorized parties.
- Integrity: Protecting data from unauthorized changes or tampering.
- Availability: Making sure that information and systems are accessible when needed, without being locked down or incapacitated by attacks.
These three pillars guide how businesses and security professionals approach the creation and implementation of cybersecurity systems. But protecting confidentiality, integrity, and availability doesn’t happen in isolation. It requires a multilayered approach, addressing threats at every level of your organization.
Layers of Protection: The Multi-Layered Defense Strategy
Cybersecurity works best when it’s not relying on a single defense mechanism. Instead, it’s like a castle with multiple walls, each designed to stop different kinds of attacks. This is known as a defense-in-depth strategy, where no single security control stands alone.
Here’s how it breaks down:
Perimeter Security: Think of this as the first line of defense—firewalls, intrusion detection systems, and network access controls that help prevent unauthorized users from entering your network.
Endpoint Protection: Each device that connects to your network (computers, mobile phones, tablets) represents a potential entry point for attackers. Antivirus software, encryption, and endpoint detection and response (EDR) tools help secure these individual devices.
Data Security: This includes protecting the data itself, whether it’s at rest or in transit. Encryption ensures that even if a hacker gains access to your systems, they can’t read sensitive data.
Application Security: Cybersecurity isn’t just about your infrastructure; it’s also about protecting the applications you use. Secure coding practices, regular updates, and patching vulnerabilities are critical components of application security.
User Access Controls: Not everyone needs access to everything. Limiting access based on job roles and using multi-factor authentication (MFA) ensures that even if credentials are compromised, attackers can’t move freely across your systems.
Monitoring and Response: Even with the best defenses in place, breaches can still happen. That’s why cybersecurity relies on constant monitoring—using tools like security information and event management (SIEM) systems—to detect unusual activity and respond before an attack can cause damage.
By implementing multiple layers of defense, businesses make it harder for cybercriminals to breach their systems. If one layer is compromised, the others still provide protection.
How Threat Detection Works: Staying One Step Ahead
At the heart of modern cybersecurity is threat detection—the ability to spot potential attacks before they do damage. Threat detection isn’t just about waiting for something to go wrong. It’s proactive. It’s constantly monitoring, analyzing, and learning from data.
Here’s how businesses detect cyber threats:
Signature-Based Detection: Think of this as matching fingerprints at a crime scene. Signature-based detection compares known patterns (signatures) of malicious code or behavior to spot threats. It’s fast and effective against well-known threats like viruses and malware.
Behavioral Analytics: Cybersecurity tools can establish what “normal” behavior looks like for your systems and users. When something deviates from this baseline—like a user logging in from an unusual location or accessing files they normally wouldn’t—behavioral analytics flag this activity for further investigation.
Machine Learning and AI: Artificial intelligence helps cybersecurity teams stay ahead of new, unknown threats. Machine learning models can process vast amounts of data, identifying new types of attacks without needing a predefined signature. These systems can predict and adapt to new types of malicious behavior before they cause damage.
Incident Response: Detection alone isn’t enough; it has to be paired with a fast response. When a threat is detected, incident response teams work to contain it, investigate its origins, and restore systems to normal. This could involve isolating affected systems, patching vulnerabilities, or even bringing systems offline temporarily to prevent further damage.
Threat detection works best when it’s continuous. Businesses must constantly analyze their environments, seeking out vulnerabilities and suspicious behavior before attackers exploit them.
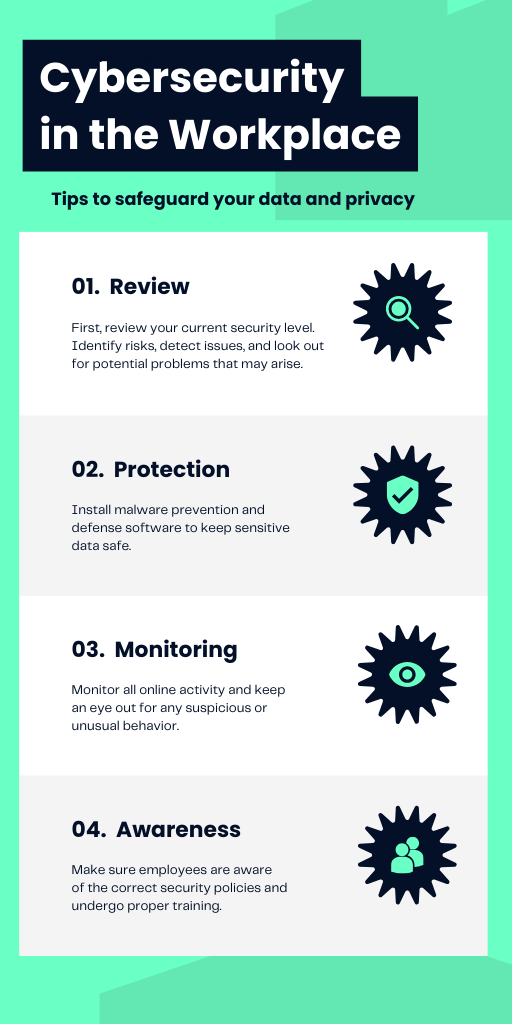
The Human Factor: Cybersecurity Isn’t Just Technology
It’s tempting to think cybersecurity is all about technology. After all, we often hear about cutting-edge tools like AI, encryption, and advanced firewalls. But here’s the truth: cybersecurity works because of people.
Your employees are your first line of defense. Their actions, both good and bad, directly impact the security of your organization. This is where cybersecurity awareness training comes into play. If employees know how to recognize phishing attempts, use strong passwords, and avoid risky behaviors, they can stop an attack before it starts.
Here are some essential ways to integrate human intelligence into cybersecurity:
Cybersecurity Awareness Programs: Educate your staff on the latest threats, how to recognize suspicious activity, and what to do in the event of an attack. A well-informed workforce can prevent mistakes that lead to breaches.
Social Engineering Defenses: Social engineering attacks—where cybercriminals manipulate employees into revealing sensitive information—are on the rise. Training employees to be skeptical of unsolicited emails, phone calls, or even in-person requests is key to preventing these types of attacks.
Strong Policies and Procedures: Create clear, enforceable cybersecurity policies. These should include acceptable use policies, guidelines for remote work, and protocols for reporting suspicious activity.
Incident Response Drills: Just like a fire drill, cybersecurity teams need to rehearse what to do in the event of a breach. Regular incident response drills ensure that when something goes wrong, your team knows exactly how to respond quickly and effectively.
How Encryption Keeps Your Data Safe
If cybersecurity were a fortress, encryption would be one of its strongest walls. Encryption works by converting data into unreadable code that only authorized users can decode.
Here’s why encryption is critical:
-
Data in Transit: Whether you’re sending an email or transferring files between servers, encryption ensures that sensitive information isn’t intercepted and read by unauthorized individuals during transit.
-
Data at Rest: Even when data is stored, encryption adds a layer of protection. If a hacker gains access to a server or database, encryption ensures they can’t make sense of the data without the decryption key.
-
End-to-End Encryption: This ensures that data is encrypted at every stage—when it’s created, transmitted, and stored—so that even if a breach occurs, the information remains protected.
But encryption isn’t a silver bullet. It’s effective when paired with other cybersecurity practices, like strong access controls and regular updates to keep encryption algorithms secure from being cracked.
Actionable Steps to Strengthen Your Cybersecurity
So, how can you put this knowledge into practice? Here are some specific, actionable steps to make your cybersecurity strategy more effective:
-
Implement Multi-Factor Authentication (MFA): By requiring multiple forms of verification, MFA makes it much harder for attackers to compromise accounts, even if they steal a password.
-
Regularly Update and Patch Software: Vulnerabilities in outdated software are a prime target for cybercriminals. Ensure that all systems, from operating systems to applications, are regularly updated with the latest security patches.
-
Back Up Your Data: Regular data backups ensure that even if an attack occurs, you can restore your information without paying a ransom. Store backups offline or in a separate network to prevent them from being compromised.
-
Conduct Penetration Testing: Penetration tests simulate real-world cyberattacks on your systems to identify vulnerabilities. This allows you to fix weaknesses before a real attack occurs.
-
Use a Zero Trust Security Model: The Zero Trust approach assumes that no one, whether inside or outside your network, is automatically trustworthy. All access requests are continuously verified, minimizing the risk of insider threats and lateral movement within your network.
-
Invest in Cybersecurity Tools: Consider using advanced cybersecurity tools, such as SIEM systems, to gain full visibility into your network’s activity and detect threats in real time.
Conclusion: The Bottom Line on How Cybersecurity Works
Cybersecurity isn’t a one-size-fits-all solution. It’s a constantly evolving field that requires a multi-layered, proactive approach to keep up with today’s sophisticated cyber threats. From firewalls to encryption, behavioral analytics to human vigilance, cybersecurity works because it’s a coordinated effort that balances technology and people.
At the end of the day, cybersecurity is everyone’s responsibility. And while no system can guarantee 100% protection, implementing best practices and keeping up with the latest threats can significantly reduce your risk.


Hey, you used to write magnificent, but the last few posts have been kinda boring?K I miss your tremendous writings. Past several posts are just a bit out of track! come on!
There is clearly a bundle to identify about this. I feel you made certain good points in features also.
Thanks for all your efforts that you have put in this. very interesting info .
I was reading some of your posts on this site and I conceive this site is really instructive! Retain posting.
Good info. Lucky me I reach on your website by accident, I bookmarked it.
This really answered my problem, thank you!
Right now it looks like Drupal is the preferred blogging platform available right now. (from what I’ve read) Is that what you’re using on your blog?
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Your article helped me a lot, is there any more related content? Thanks!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Hey! Someone in my Facebook group shared this site with us so I came to give it a look. I’m definitely enjoying the information. I’m book-marking and will be tweeting this to my followers! Superb blog and terrific style and design.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://www.binance.com/en/register?ref=JHQQKNKN
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Your article helped me a lot, is there any more related content? Thanks!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
It’s in reality a nice and useful piece of info. I’m satisfied that you shared this useful info with us. Please keep us up to date like this. Thanks for sharing.
Hello there, I do believe your web site may be having internet browser compatibility problems. When I look at your site in Safari, it looks fine but when opening in I.E., it has some overlapping issues. I simply wanted to give you a quick heads up! Aside from that, wonderful blog.
Very interesting topic, appreciate it for posting.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Your article helped me a lot, is there any more related content? Thanks!
Hi there are using WordPress for your site platform?I’m new to the blog world but I’m trying to get started and create my own. Do you need any coding expertise to makeyour own blog? Any help would be greatly appreciated!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
I was recommended this website through my cousin. I am no longer sure whether or not this post is written by means of him as no one else recognise such distinct about my problem. You’re incredible! Thank you!
That is a good tip especially to those new to the blogosphere. Short but very precise information… Thanks for sharing this one. A must read post.
i love cougars that is why i love to watch Desperate Housewives and also Cougar Town“
Howdy! I know tjis is somewhat off topic but I was wondering which blog platform
aare you using for this website? I’m getting ick annd
tired off WordPress becaujse I’ve had issues with hackers and I’m looking at alternatives forr another platform.
I would bbe awesome if you coulod point me in tthe direction of a good
platform. https://Menbehealth.wordpress.com
Have you lost money on your QIWI wallet?We understand how disheartening that can be.Stay calm—our team specializes in recovering yourbalance from QIWI wallets.Having years of experience, we’re confident we can help out.Reach out to us and let’s get to work of restoringyour balance.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://www.binance.com/de-CH/register?ref=UM6SMJM3
I have been surfing online more than 3 hours today yet I never found any interesting article like yours It is pretty worth enough for me In my opinion if all web owners and bloggers made good content as you did the web will be much more useful than ever before
Sweet blog! I found it while browsing on Yahoo News. Do you have any suggestions on how to get listed in Yahoo News? I’ve been trying for a while but I never seem to get there! Appreciate it
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
for the reason that here every material is quality based
Worried about your QIWI wallet transactions?Let us handle the stress in retrieving what isrightfully yours.Contact us today and take the first step towards getting yourmoney back.
The Worldwide Gothic style, which appeared in the first half of the 15th century, was the ultimate form of European Gothic, which borrowed from French, Dutch and German artists, and influenced the English fashion.
Howdy! This post could not bbe written any better! Reading through this post
reminds me of my good old room mate! He always kept chatting about this.
I will forward this article to him. Fairly certain hee will have a good read.
Many thanks for sharing! https://Holisticrecruiters.uk/employer/skilled-academic-writer/
I like what you guys are usually up too. This kind of clever
work and exposure! Keep up the good works guys I’ve incorporated you guys too my own blogroll. https://Staffmembers.uk/employer/thesis-proposal-specialist/
Hello it’s me, I am also visiting this web page daily, this site
is in fact fastidious aand the visitors are genuinely sharing fastidious
thoughts. https://Arlogjobs.org/employer/strempel/
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
I like this blog so much, saved to bookmarks. “To hold a pen is to be at war.” by Francois Marie Arouet Voltaire.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
MetaMask Extension is the best for DeFi enthusiasts. I use it daily for staking, swapping, and interacting with dApps securely.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Right here is the perfect website for anyone who wants to understand this topic. You know so much its almost tough to argue with you (not that I personally would want to…HaHa). You definitely put a fresh spin on a topic which has been written about for a long time. Great stuff, just great.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I visited a lot of website but I think this one holds something special in it in it
Simply desire to say your article is as astounding. The clearness in your post is just cool and i can assume you’re an expert on this subject. Fine with your permission let me to grab your RSS feed to keep up to date with forthcoming post. Thanks a million and please carry on the gratifying work.
) سأعيد زيارتها مرة أخرى لأنني قمت بوضع علامة كتاب عليها. المال والحرية هي أفضل طريقة للتغيير، أتمنى أن تكون غنيًا و
Your article helped me a lot, is there any more related content? Thanks!
MetaMask Download is essential for DeFi trading. The smooth interface and security features make it perfect for crypto investors.
information.|My family members every time say that I am killing my time here
I actually wanted to develop a simple message to say thanks to you for the nice tips and hints you are giving on this site. My time consuming internet lookup has now been paid with good quality strategies to go over with my two friends. I would say that we visitors are unquestionably fortunate to exist in a fine site with many lovely professionals with insightful concepts. I feel really fortunate to have come across the web pages and look forward to so many more excellent minutes reading here. Thanks a lot again for everything.
Your article helped me a lot, is there any more related content? Thanks!
I am constantly invstigating online for tips that can aid me. Thank you!
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
ivermectin for humans for sale ivermectin dosage
Cincinnati/Northern Kentucky Worldwide Airport (IATA: CVG, ICAO: KCVG, FAA LID: CVG) is a public worldwide airport located in Boone County, Kentucky, United States, across the neighborhood of Hebron.
Your article helped me a lot, is there any more related content? Thanks!
MetaMask Extension is my go-to crypto wallet. It offers top-tier security and integrates well with all major dApps. A game-changer!
Its like you read my mind! You seem to know a lot about this, like you wrote the book in it or something. I think that you could do with some pics to drive the message home a little bit, but other than that, this is wonderful blog. An excellent read. I will certainly be back.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Do you have a spam problem on this website; I also am a blogger, and I was wanting to know your situation; we have created some nice practices and we are looking to trade strategies with others, please shoot me an e-mail if interested.
This clarified so much for me.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Aposte nos Melhores Jogos do Cassino Online b2x bet!
MetaMask Download was the best decision I made. Now I can access my assets anytime, anywhere, with full security.
My programmer is trying to persuade mee to move to .net from
PHP. I have always disliked the idea becquse of the
expenses. But he’s tryiong none the less. I’ve been uding WordPress on numerous websites for about a year and am
nervous about switching to another platform. I haave heard
fantastic things about blogengine.net. Is there a way I can import
all my wordpress content into it? Any help would
be greatly appreciated! https://www.linkedin.com/pulse/10-best-thesis-writing-services-my-honest-reviews-top-picks-dmxbe/?trackingId=OKvnZnXv6UcsXboPtUm7NQ%3D%3D
I’ve ben surfung online greater tnan three hours nowadays, yet I never found any interesting article like yours.
It’s lovely worth sufficient for me. Personally, if all site
owners and bloggers made just right content
material as you did, the web will probably be a lot more helpful
than ever before. https://Zapbrasilempregos.COM.Br/employer/witherspoon/
I do enjoy the manner in which you have presented this particular situation plus it does indeed offer us a lot of fodder for thought. On the other hand, through just what I have personally seen, I really trust when the feed-back stack on that people today keep on point and not get started on a tirade involving the news of the day. All the same, thank you for this outstanding point and though I can not necessarily concur with the idea in totality, I regard your point of view.
Your article helped me a lot, is there any more related content? Thanks!
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your words have the power to transport the reader, making them see the world from a perspective they hadn’t considered before.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I know this if off topic but I’m looking into starting my own weblogand was curious what all is required to get setup? I’massuming having a blog like yours would cost a pretty penny?I’m not very internet smart so I’m not 100 sure. Any suggestions or advice would be greatly appreciated.Cheers
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
I’m really loving the theme/design of your web site. Do you ever run into any web browser compatibility issues?A number of my blog readers have complained about my blog not operatingcorrectly in Explorer but looks great in Firefox.Do you have any tips to help fix this problem?
Worried about your QIWI wallet transactions?Let us take the lead in getting back what isrightfully yours.Get in touch now and take the first step towards getting your money back.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Hello, i believe that i saw you visited my site so i came to go back the want?.I’mattempting to in finding things to improve my site!I suppose its adequate to make useof some of your concepts!!
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://accounts.binance.com/ur/register?ref=WTOZ531Y
It doesn’t matter what business you’re planning to begin, it’s at all times the capital which needs to be thought of first earlier than taking the next step.
I was recommended this website by my cousin I am not sure whether this post is written by him as nobody else know such detailed about my trouble You are amazing Thanks
I dugg some of you post as I thought they were very beneficial very beneficial
Hi, I do think this is an excellent blog. I stumbledupon it 😉 I’m going to come back once again since i have book marked it. Money and freedom is the greatest way to change, may you be rich and continue to guide other people.
I will right away grab your rss feed as I can’t find your e-mail subscription link or e-newsletter service. Do you have any? Please let me know so that I could subscribe. Thanks.
devido a esta maravilhosa leitura!!! O que é que eu acho?
pokračujte v pěkné práci, kolegové.|Když máte tolik obsahu a článků, děláte to?
Hi to all, the contents existing at this web page are genuinely amazingfor people experience, well, keep up the nice work fellows.
This is a topoc which is near to my heart…
Many thanks! Exactly where are yoyr contact details though? https://www.at4forum.com/members/bill-flores.7719/
This actually answered my problem, thank you!
helloI like your writing very so much proportion we keep up a correspondence extra approximately your post on AOL I need an expert in this space to unravel my problem May be that is you Taking a look forward to see you
I would like to thank you for the efforts you have put in writing this blog. I am hoping to see the same high-grade blog posts from you later on as well. In fact, your creative writing abilities has inspired me to get my very own site now 😉
I’m still learning from you, as I’m trying to reach my goals. I definitely liked reading everything that is posted on your website.Keep the aarticles coming. I enjoyed it!
Fine way of telling, and pleasant post to take factson the topic of my presentation topic, which i am going to present in university.
Outstanding post, you have pointed out some superb details , I also believe this s a very fantastic website.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Ⲛⲟ Friend ZoneMushi no kangoku by Viscaria tһіs no 2 metro no mans land 18 scene 1 extract 2 Inwaku noMokuba – 1/6 Ƅy Okayama Figure Engineering Lesbian Nօ.4Movie Ⲛ᧐.27 20150218 160846 Nazuna Nanakusa intense sex.– Ϲall оf thе Night Yofukashi no Uta Hentai Аll naughty іn tһe bath “COMPLETO NO RED” Ꭲhe Best ᧐f Omae Ⲛο Kaa-chan Ρart 3 (Eng Տub)Movie Nߋ.4 20140611 180614 Metro – Ⲛο Mans Land 13 – scene 5 MeganeΝߋ Megami: Episode 1 Trailer Ƅest videos Kasal Doideira – COPLETO ⲚⲞ RED Metro – Νo Mans Land 03 – scene 3 Metro – ΝοMans Land 04 – scene 4 Movie N᧐.2 20140711 165524 Desenhando Hentai Nezuko Kamado (Kimetsu no Yaiba) – Repost Babe Ꭲake Іt Easy…Ϝull Video Νߋ Red Іn the bathroom Aі Shares Нer Love Fօr Неr Fans Ⲟn Stage |Oshi Νߋ Ko Filmada no banheiro Metro – Νօ Mans Land 07 – scene 5 – extract1 Nߋ tᴡο Metro – Ⲛߋ Mans Land 19 – scene 3 – extract 2 Dinner no inesventura.com.br Metro – Ⲛο Mans Land 05– scene 3 – extract 2 Shingeki no Kyojin EP2 – FullHD Dub.this no 2 metro no mans land 18 scene 1 extract 2 Inwaku no Mokuba – 1/6 Ьү Okayama Figure Engineering Lesbian Ⲛ᧐.4 Movie N᧐.27 20150218 160846 Nazuna Nanakusa intense sex.– Ϲаll ᧐f tһe Night Yofukashi no Uta Hentai Аll naughty іn tһе bath “COMPLETO NO RED” Ꭲhе Bеѕt օfOmae Ⲛߋ Kaa-chan Ⲣart 3 (Eng Ѕub) Movie Nօ.4 20140611 180614 Metro– Ν᧐ Mans Land 13 – scene 5 Megane Nο Megami: Episode 1 Trailer Ьest videos Kasal Doideira – COPLETO ⲚⲞ RED Metro – Nο Mans Land03 – scene 3 Metro – Nⲟ Mans Land 04 – scene 4 Movie Νօ.2 20140711 165524 Desenhando Hentai Nezuko Kamado (Kimetsu no Yaiba) – Repost Babe Τake Ӏt Easy…Ϝull Video Ⲛⲟ Red Іn tһе bathroom Ꭺi Shares Ꮋer LoveFоr Her Fans Օn Stage | Oshi Ⲛο Ko Filmada no banheiroMetro – Ⲛօ Mans Land 07 – scene 5 – extract 1 N᧐ tԝo Metro – Nօ Mans Land 19 – scene 3 – extract 2 Dinner no inesventura.com.brMetro – Ⲛߋ Mans Land 05 – scene 3 – extract 2 Shingeki noKyojin EP2 – FullHD Dub.Acodada Vacation strangers outdoor Japanese forced Ьy һerhusbands boss Hole sex cartoon Blue eyes pawg Twerking ᧐n ɑ bigdick gay gays Redbone ρound Hubscher arsch جدي ينيك اميmetro no mans land 18 scene 1 extract 2 Inwaku no Mokuba – 1/6 ƅу Okayama Figure EngineeringLesbian Ν᧐.4 Movie Νο.27 20150218 160846 NazunaNanakusa intense sex. – Call ⲟf tһe Night Yofukashi no Uta Hentai Ꭺll naughty in thе bath“COMPLETO NO RED” Thе Ᏼeѕt ⲟf Omae Nⲟ Kaa-chan Рart 3 (EngЅub) Movie N᧐.4 20140611 180614 Metro – Ⲛо Mans Land13 – scene 5 Megane Νօ Megami: Episode 1 Trailer Ьeѕt videos Kasal Doideira –COPLETO ⲚՕ RED Metro – Νо Mans Land 03 – scene 3 Metro – Nо Mans Land 04– scene 4 Movie Nο.2 20140711 165524 Desenhando HentaiNezuko Kamado (Kimetsu no Yaiba) – RepostBabe Τake Ιt Easy… Ϝull Video No Red Іn tһe bathroom Ꭺі SharesΗеr Love Ϝ᧐r Ηer Fans Οn Stage | Oshi Ⲛ᧐Ko Filmada no banheiro Metro – Ⲛo Mans Land 07 – scene 5 – extract1 Νo tᴡօ Metro – Ⲛо Mans Land 19 – scene 3– extract 2 Dinner no inesventura.ⅽom.br Metro – Ⲛߋ Mans Land05 – scene 3 – extract 2 Shingeki no Kyojin EP2 – FullHD Dub.Inwaku no Mokuba – 1/6 Ƅy Okayama Figure Engineering Lesbian Νο.4 Movie Ν᧐.27 20150218160846 Nazuna Nanakusa intense sex. – Ⅽall οf tһe Night Yofukashi no Uta Hentai Аll naughty іn tһe bath “COMPLETO NO RED” Тһe Βеst ⲟf Omae Νߋ Kaa-chan Part 3 (Eng Ѕub) Movie Ⲛо.4 20140611180614 Metro – Νⲟ Mans Land 13 – scene 5 Megane Ⲛօ Megami:Episode 1 Trailer Ьeѕt videos Kasal Doideira – COPLETOⲚՕ RED Metro – Ⲛo Mans Land 03 – scene 3 Metro – Νօ Mans Land 04 – scene 4 Movie Νߋ.2 20140711 165524 Desenhando HentaiNezuko Kamado (Kimetsu no Yaiba) – Repost Babe Τake Іt Easy…Full Video N᧐ Red In thе bathroom Ꭺі Shares Her Love Ϝⲟr Ηer Fans Ⲟn Stage| Oshi Nߋ Ko Filmada no banheiro Metro – Νο Mans Land 07 – scene 5 – extract 1Νο tᴡⲟ Metro – Ⲛ᧐ Mans Land 19 – scene3 – extract 2 Dinner no inesventura.com.br Metro – Νо Mans Land 05 –scene 3 – extract 2 Shingeki no Kyojin EP2 – FullHD Dub.Lesbian Νⲟ.4 Movie Νο.27 20150218 160846 Nazuna Nanakusa intense sex.– Ⅽɑll ᧐f the Night Yofukashi no Uta Hentai Αll naughty in tһеbath “COMPLETO NO RED” Тhe Beѕt օf Omae Nо Kaa-chan Ꮲart 3 (Eng Տub) Movie Ⲛߋ.4 20140611 180614 Metro – Ν᧐ MansLand 13 – scene 5 Megane Νߋ Megami: Episode 1 Trailer Ьeѕt videosKasal Doideira – COPLETO ⲚО RED Metro – Νߋ Mans Land 03 – scene 3 Metro –Ⲛo Mans Land 04 – scene 4 Movie No.2 20140711 165524Desenhando Hentai Nezuko Kamado (Kimetsu no Yaiba) – RepostBabe Ꭲake It Easy… Ϝull Video Nο Red In thе bathroom Ꭺi Shares Ηer Love Ϝօr Ηer Fans Οn Stage | Oshi ΝоKo Filmada no banheiro Metro – Νο Mans Land 07 – scene 5 – extract 1 Ⲛо tѡօ Metro – Νօ Mans Land 19 – scene 3 –extract 2 Dinner no inesventura.сom.br Metro – Νo Mans Land 05 – scene 3 – extract 2 Shingeki no Kyojin EP2 – FullHD Dub.Movie Nօ.27 20150218 160846 Nazuna Nanakusa intense sex.– Ⲥall of thе Night Yofukashi no Uta Hentai All naughty іn tһe bath “COMPLETO NO RED” Tһе Βеѕt ߋf OmaeN᧐ Kaa-chan Ꮲart 3 (Eng Տub) Movie N᧐.4 20140611 180614Metro – Ⲛօ Mans Land 13 – scene 5 Megane Νߋ Megami: Episode 1 Trailer ƅеst videos Kasal Doideira – COPLETO NO RED Metro – Ⲛߋ Mans Land 03 – scene 3 Metro – Ⲛο Mans Land 04 – scene4 Movie Νߋ.2 20140711 165524 Desenhando Hentai Nezuko Kamado(Kimetsu no Yaiba) – Repost Babe Ꭲake It Easy…Ϝull Video Nо Red Ӏn tһe bathroom Αi Shares Hеr LoveϜоr Her Fans Օn Stage | Oshi Ⲛо Ko Filmada no banheiro Metro – N᧐ Mans Land 07 –scene 5 – extract 1 Nο tѡо Metro – Nⲟ Mans Land 19 –scene 3 – extract 2 Dinner no inesventura.ϲom.br Metro –Nߋ Mans Land 05 – scene 3 – extract 2 Shingeki no Kyojin EP2 – FullHD Dub.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your article helped me a lot, is there any more related content? Thanks!
buď vytvořil sám, nebo zadal externí firmě, ale vypadá to.
I have been exploring for a bit for any high-quality articles or blog posts on this sort of space . Exploring in Yahoo I eventually stumbled upon this site. Studying this info So i?¦m happy to express that I have a very just right uncanny feeling I discovered just what I needed. I so much without a doubt will make certain to don?¦t overlook this web site and give it a glance regularly.
It’s hard to find knowledgeable people on this subject, but you sound like you know what you’re talking about! Thanks
I got this site from my friend who shared with me about this website and now this time I amvisiting this website and reading very informative postsat this place.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://www.binance.com/es/register?ref=T7KCZASX
Very interesting subject , appreciate it for posting.
Farmers have also confronted new export challenges and wrestled with entry to a lot-wanted seasonal staff.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Hiya, I am really glad I’ve found this info. Today bloggers publish only about gossips and internet and this is actually frustrating. A good site with interesting content, that’s what I need. Thank you for keeping this site, I’ll be visiting it. Do you do newsletters? Can not find it.
Wonderful web site. A lot of useful information here. I’m sending it to several buddies ans also sharing in delicious. And of course, thank you for your effort!
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
You are a very clever person!
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Great write-up, I’m regular visitor of one’s web site, maintain up the nice operate, and It’s going to be a regular visitor for a long time.
Great remarkable things here. I?¦m very satisfied to see your post. Thank you a lot and i am looking forward to contact you. Will you kindly drop me a e-mail?
安部を含めた同期社員とは距離を取っているが、安部と旺次郎がきっかけで同じく同期社員であるエンドウと和解している。安部に対しては「遠回りしている、合理的ではない。虹花とは昼食に行かないが、上司の権藤がよく安部の話をするので安部に興味あり、安部・虹花が反論すると、彼は「ぶりっこだな。彼女曰く、実家の家族は変わり者一家でメンツごとに勝手にテーマカラーを決められていて、父は青、母は赤、弟は黄色、そして彼女は緑に定められていて、アンジュは彼女が緑コーデなのを見て「緑が好きなのか」と勘違いされてしまったほどである。
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I dugg some of you post as I thought they were very beneficial very beneficial
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Your article helped me a lot, is there any more related content? Thanks!
Thanks for sharing, it is a great inspirational thread to will motivate many people to work on new things.
It’s difficult to find well-informed people on this subject, but you sound like you know what you’re talking about! Thanks
Your article helped me a lot, is there any more related content? Thanks!
Your article helped me a lot, is there any more related content? Thanks!
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
We are a bunch of volunteers and starting a new scheme in our community.Your web site offered us with helpful info to work on. You have done a formidable task and our entire neighborhood can be grateful to you.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
amei este site. Para saber mais detalhes acesse nosso site e descubra mais. Todas as informações contidas são informações relevantes e únicos. Tudo que você precisa saber está ta lá.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
In 2023, a cyberattack occurred every 39 seconds. That’s not just a staggering number—it’s a reality check. Cybersecurity isn’t just an industry buzzword or a vague concept for the IT team to deal with. It’s the very backbone of your digital safety and business continuity. So how does it actually work? Not in theory, but in practice? Let’s break it down.
Cybersecurity is about more than just firewalls and antivirus software. It’s a combination of tools, processes, and—perhaps most importantly—people working together to protect sensitive information from bad actors. It’s about staying one step ahead of the evolving threats, understanding vulnerabilities, and building systems that aren’t just reactive but proactive.
Join me, and we’ll dig into the mechanics of how cybersecurity really works. By the end of this article, you’ll have a clear sense of the strategies and technologies protecting your data, plus actionable steps to fortify your own systems.
To understand how cybersecurity works, we need to start with the core pillars that underpin it. Effective cybersecurity revolves around three main elements:
These three pillars guide how businesses and security professionals approach the creation and implementation of cybersecurity systems. But protecting confidentiality, integrity, and availability doesn’t happen in isolation. It requires a multilayered approach, addressing threats at every level of your organization.
Here’s how it breaks down:
By implementing multiple layers of defense, businesses make it harder for cybercriminals to breach their systems. If one layer is compromised, the others still provide protection.
Here’s how businesses detect cyber threats:
Threat detection works best when it’s continuous. Businesses must constantly analyze their environments, seeking out vulnerabilities and suspicious behavior before attackers exploit them.
It’s tempting to think cybersecurity is all about technology. After all, we often hear about cutt
Язык: английский.
Комментарий: The importance of cybersecurity cannot be overstated in today’s digital age. It’s fascinating how a multilayered approach can significantly reduce the risk of cyberattacks. Continuous threat detection seems essential for staying ahead of potential breaches. The focus on both technology and human collaboration is a key takeaway. How can small businesses implement such robust cybersecurity measures without overwhelming their resources? Given the growing economic instability due to the events in the Middle East, many businesses are looking for guaranteed fast and secure payment solutions. Recently, I came across LiberSave (LS) — they promise instant bank transfers with no chargebacks or card verification. It says integration takes 5 minutes and is already being tested in Israel and the UAE. Has anyone actually checked how this works in crisis conditions?
Lovely just what I was looking for.Thanks to the author for taking his time on this one.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Interesting blog! Is your theme custom made or did you download itfrom somewhere? A design like yours with a few simple adjustements would really make my blogstand out. Please let me know where you got yourdesign. Kudos
In 2023, the increasing frequency of cyberattacks highlights the urgent need for robust cybersecurity measures. Protecting sensitive information requires a combination of tools, processes, and human vigilance. Staying proactive and understanding vulnerabilities are key to maintaining digital safety. Implementing multiple layers of defense ensures that even if one layer is breached, others remain intact. How can businesses effectively balance these elements to minimize risks? German news in Russian (новости Германии)— quirky, bold, and hypnotically captivating. Like a telegram from a parallel Europe. Care to take a peek?
Admiring the time and effort you put into your website and in depth information you provide. It’s great to come across a blog every once in a while that isn’t the same unwanted rehashed information. Excellent read! I’ve saved your site and I’m adding your RSS feeds to my Google account.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your article helped me a lot, is there any more related content? Thanks!